by Nadet Rautenbach | Apr 22, 2024 | Business Intelligence, Data Integration, Routing and Scheduling
Optimizing Routes for Improved Fleet Management In fleet management, optimizing routes plays a pivotal role in enhancing efficiency, reducing costs, and improving overall performance. Fleetistics is excited to announce significant enhancements in our Route4Me...
by Nadet Rautenbach | Mar 27, 2024 | Data Integration
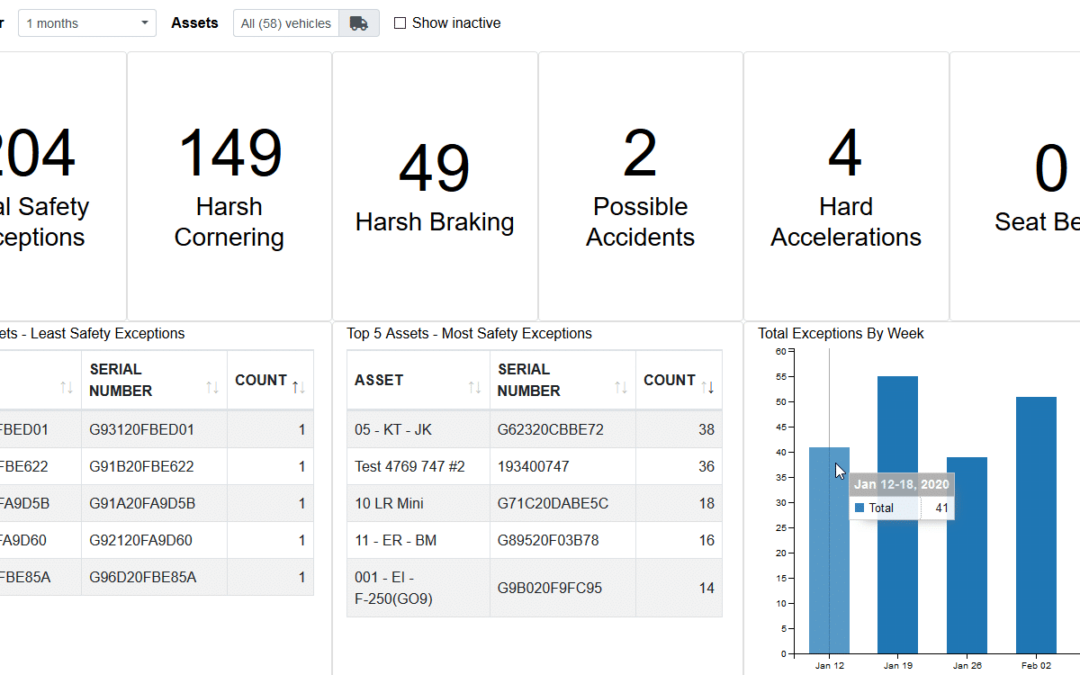
Unlocking Efficiency: How Real-Time Data Transforms Fleetistics Operations Is having a plethora of data always beneficial? As the data landscape expands exponentially, this question becomes increasingly critical. Projections indicate that by 2025, there will be almost...
by Lynn Rios | Oct 27, 2023 | Fleet Management, Data Integration, Fleet Management Software
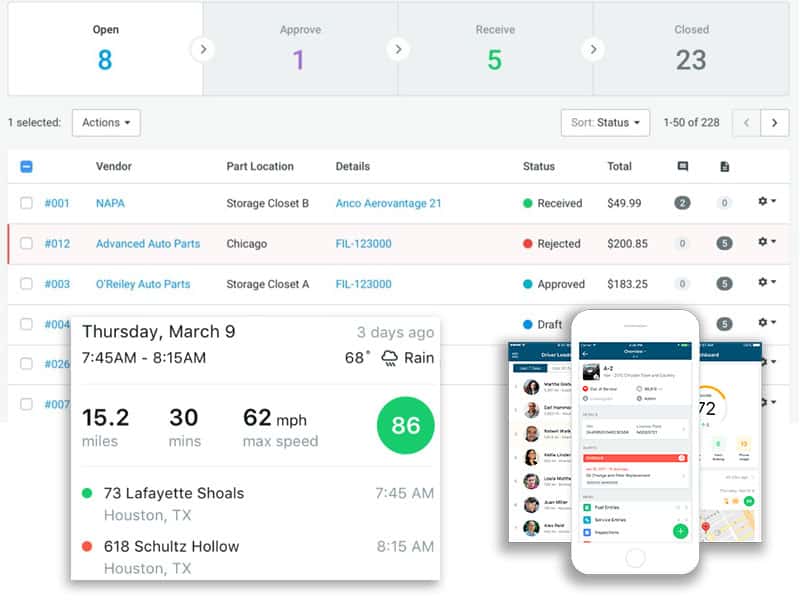
Fleetio Fleet Management, The Ultimate Maintenance Solution Looking for an integrated maintenance solution? Integrated with Geotab, Fleetio Fleet Management empowers your team to manage vehicles, equipment, maintenance, total cost of ownership, fuel, and more with...

by Nadet Rautenbach | Oct 13, 2023 | Data Integration, Government Fleet, GPS Tracking & Telematics Equipment
In today’s rapidly changing world, the significance of accurate and efficient public transport cannot be overstated. With the prevalent use of displacement sensing devices such as GPS tracking systems and smart cards, modernizing public transport has become a...

by Lynn Rios | Jun 21, 2021 | Data Integration, ROI
Electronic Signature Defined An electronic signature or e-signature, according to Wikipedia, refers to data in electronic form, which is logically associated with other data in electronic form and which is used by the signatory to sign. This type of signature has the...
by Eron Iler | Apr 12, 2021 | Data Integration, Fleet Management Software, Resources
Custom GPS Vehicle Tracking System – Can I do it myself? Some people may ask this question thinking how hard can it be to create a do it yourself GPS vehicle tracking system. There is a website, GPS trackers on Amazon, and SIM cards are available at your local...