Fleet Security
Cyber Security for Fleet Management
Unlock Efficiency, Control Costs, and Drive Success.
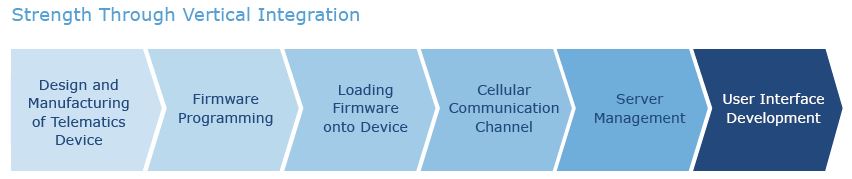
Fleet Security in Layers
- Employees
- Data Centers
- Access Control
- Data Transmission
- Systems Access
- Input Controls
- Monitoring
- GPS Device
Penetration Testing - Audit
- Security Scans
- Data Retention
- Business Continuity
Fleet Security for Mobile Devices
As vehicles become more connected mobile fleet security requirements must adapt to new threats. Any electronic device which can send and receive information is subject to a cyber attack. If the data is transmitted securely it must still be protected while being transmitted, in route through the internet and while being stored for customer access. The number of technologies involved in this process make this a challenging process that must be managed to mitigate risk. There is no such thing as zero or no risk. Risk is measured as a probability and weighed against the potential benefits.
What Goes In, Can Come Out
Understanding that the nature of the data input, increases the risk if you assume the worst which is data falling into the wrong hands. By avoiding entering data entry that has significant value, you can minimize the impact if a security breach takes place. An example would be to avoid entering specific personal information about a driver, such as a drivers license.
Hide in Plain Sight
One of the best methods of avoiding detection is to look like everyone else or have your data look like all the other. Creating a special, secret process only serves to generate curiosity and focus for a cyber attacker. With billions of data points collected every day by over 500,000 Geotab devices, it is easy for data to mix together into a pool unrecognizable from prying eyes. To further complicate a hackers life, the data is encrypted at 2048-bit SSL for all data coming and going from the server.
Read ZDNet Article
Five Key Questions to Ask Your Telematics Provider
Fleet Security is a complex topic that deals with every part of a telematics system. Simply asking is our data secure?
is not enough. With valuable data on the line, your questions should aim deeper. Look for specific implementations
and strategies that form the very basis of modern security standards. The following questions are intended to serve
as a primer to help you engage telematics providers about the security of your telematics data.
- Who manufacturers the telematics hardware? Will the device be the same across
my entire fleet?
Why It Is Important To Ask: If your telematics provider does not manufacture their own hardware,
they may not have good insight into the security of the hardware. Similarly, if your provider does not have
direct control over their hardware and software security, they may take longer to respond to threats or
vulnerabilities because they will need to coordinate with third parties.
Moreover, electronics are updated frequently. Different hardware models can introduce different sets of
vulnerabilities for each model, meaning that more work will need to be done to patch these security holes
across the entire product line. With more hardware variants, there is a higher demand on the engineers to
maintain and fix security flaws in this way resources may not be evenly spread and attention might waver
because of product complexity, which can lead to omissions and unfound vulnerabilities. Manufacturers
must be the ones responsible for security for the life of the product.
2. Do you encrypt the data as it is sent over the cellular network?
Why It Is Important To Ask: Cellular carriers should not be exclusively relied upon to secure the delivery
of your telematics data over the air. It is important that your telematics providers take additional steps to
encrypt your data so that even if the cellular communication channel is compromised, your data will not be.
3. Is the firmware signed to prevent outside parties from changing the code on the
device?
Why It Is Important To Ask: The firmware is the brain behind the device. It decides where the data
is sent, what data is captured, and how it is stored. If a malicious firmware were installed on your device,
it would no longer be possible to know where your data is being sent or what is happening to it. Your
telematics provider should sign every firmware update with a digital signature that indicates the update
came from a trusted source.
4. Do you have security documentation that covers your hardware, your servers,
the transmission of data, as well as policies for employees?
Why It Is Important To Ask: Security documentation shows a baseline commitment to a culture of
security. A telematics provider should be able to provide details on their security measures, as well as their
mitigation and disaster recovery strategies in case something unexpected occurs.
5. In the event that your servers are compromised, what sort of mitigation strategy
do you use to protect the account information of your users?
Why It Is Important To Ask: If a security breach does occur, the system should contain as little personal
information as possible. Passwords should never be stored directly in the system of your telematics provider;
rather, passwords should be transformed into hashes and further strengthened through salting.
Summary
The security of your telematics data should not be overlooked. Like any other critical business data, it should be
protected with comprehensive security mechanisms and processes that are continuously reviewed and updated.
Following industry best practices is essential.
Cybersecurity is a shared responsibility. We can all play a role in keeping security systems strong. Getting informed
and asking questions is a great first step on the path to effective cybersecurity management.
To learn more about telematics security, please visit: security.geotab.com


